The “Public” Database Role in SQL Server is a special database role that is given by default to all logins. You cannot remove a login’s membership to this role because this behavior is built into SQL Server.
What does the “Public” database role does in SQL Server?
Should we make use of it or at the end of the day just ignore it?
When you create a new login (and consequently a new database user) in SQL Server and do not give it any permissions anywhere (that is securable objects), then this database user inherits the permissions the public database role has.
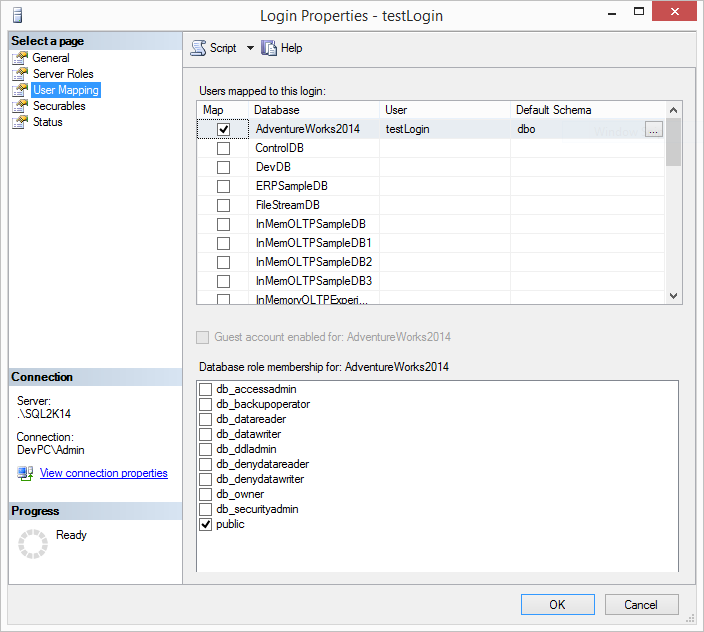
So, let’s see an example. On a SQL Server 2014 instance I have just created a login named ‘testLogin’ (not quite unique, isn’t it? 🙂 and just granted access to the ‘Adventureworks2014’ database without doing anything else. As you can see from the below screenshot, my login was just granted the Public database role on the database.
The question now is what permissions the ‘testLogin’ inherited on AdventureWorks2014? I have not provided any permission so it’s just the permissions provided by the Public database role.
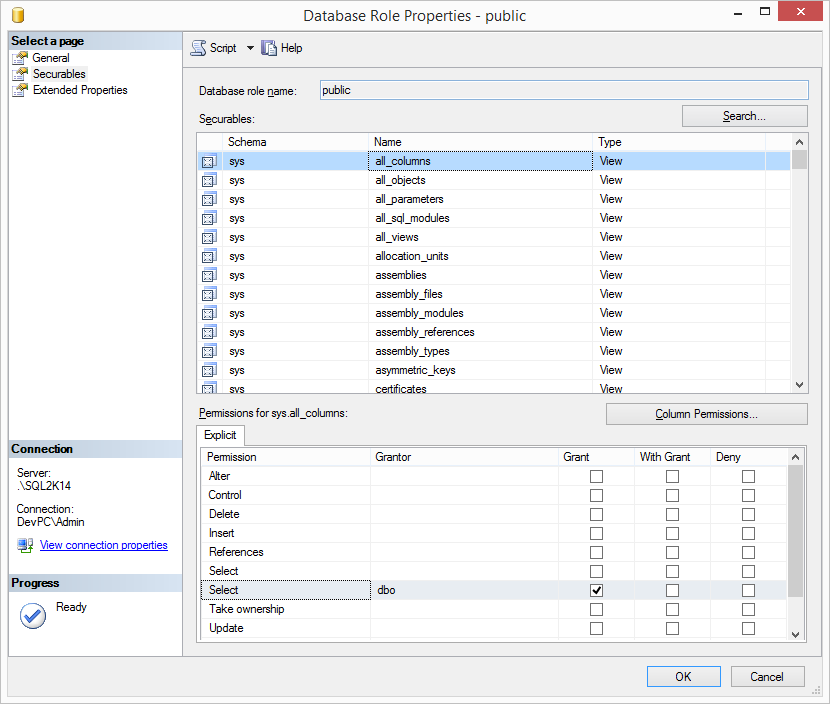
If we check the securableS for the Pulbic database role in AdventureWorks2014 security, we can see that the Public database role is granted with SELECT access to certain system catalog views such as:
-
- sys.all_columns
- sys.all_objects
- sys.all_parameters
- sys.all_sql_modules
- sys.all_views
- sys.allocation_units
- sys.assemblies
- etc.
Security recommendation about the “Public” database role in SQL Server
USE [Database Name]; GO SELECT DB_NAME() as DBName, pm.[permission_name] as PermissionName, ob.[name] as ObjectName, pm.class_desc as ObjectType, ob.type_desc as TypeDescription FROM sys.database_permissions pm INNER JOIN sys.database_principals pr ON pm.grantee_principal_id= pr.principal_id LEFT JOIN sys.objects ob ON pm.[major_id] = ob.[object_id] WHERE [state]='G' and major_id>=0 and pr.[name]='public' and ob.[name] IS NOT NULL; GO
Strengthen your SQL Server Administration Skills – Enroll to our Online Course!
Check our online course on Udemy titled “Essential SQL Server Administration Tips”
(special limited-time discount included in link).
Via the course, you will learn essential hands-on SQL Server Administration tips on SQL Server maintenance, security, performance, integration, error handling and more. Many live demonstrations and downloadable resources included!

Featured Online Courses:
- SQL Server Security Best Practices
- AI Demystified: A 1-Hour Beginner’s Guide (Suitable for Non-Technical People)
- AI Essentials: A Beginner’s Guide to Artificial Intelligence
- Human-AI Synergy: Teams and Collaborative Intelligence
- Data Management for Beginners – Main Principles
- SQL Server 2022: What’s New – New and Enhanced Features
- Working with Python on Windows and SQL Server Databases
- Introduction to Azure Database for MySQL
- Boost SQL Server Database Performance with In-Memory OLTP
- Introduction to Azure SQL Database for Beginners
- Essential SQL Server Administration Tips
- SQL Server Fundamentals – SQL Database for Beginners
- Essential SQL Server Development Tips for SQL Developers
- Introduction to Computer Programming for Beginners
- .NET Programming for Beginners – Windows Forms with C#
- SQL Server 2019: What’s New – New and Enhanced Features
- Entity Framework: Getting Started – Complete Beginners Guide
- A Guide on How to Start and Monetize a Successful Blog
Other SQL Server Security-Related Articles
- DBA Security Advisor v2.3 is Now Out!
- Essential SQL Sever Administration Tips
- Why You Need to Secure Your SQL Server Instances
- SQL Server Row Level Security by Example
- Should Windows “Built-In\Administrators” Group be SQL Server SysAdmins?
- Policy-Based Management in SQL Server
- Frequent Password Expiration: Time to Revise it?
- Encrypting SQL Server Databases
- Transparent Data Encryption (TDE) in SQL Server
- 10 Facts About SQL Server Transparent Data Encryption
- Encrypting a SQL Server Database Backup
- What is Data Security and which are its Main Characteristics?
- …check all
Subscribe to the GnoelixiAI Hub newsletter on LinkedIn and stay up to date with the latest AI news and trends.
Subscribe to the SQLNetHub YouTube channel (SQLNetHub TV).
Subscribe to my personal YouTube channel.
Rate this article:
Reference: SQLNetHub.com (https://www.sqlnethub.com)
© SQLNetHub
Artemakis Artemiou is a seasoned Senior Database and AI/Automation Architect with over 20 years of expertise in the IT industry. As a Certified Database, Cloud, and AI professional, he has been recognized as a thought leader, earning the prestigious Microsoft Data Platform MVP title for nine consecutive years (2009-2018). Driven by a passion for simplifying complex topics, Artemakis shares his expertise through articles, online courses, and speaking engagements. He empowers professionals around the globe to excel in Databases, Cloud, AI, Automation, and Software Development. Committed to innovation and education, Artemakis strives to make technology accessible and impactful for everyone.